Innovative companies specifically benefit from their intellectual achievements, more than from the simple distribution of directly tangible products. Trade secrets are often a sensible way of protecting development in such a context. The corresponding prerequisites are set out in the German Law on the Protection of Trade Secrets (GeschGehG), which implements a European directive with some delay. We highlight the requirements and the resulting need for action.
- If the added value of the company lies primarily in intellectual activity, the core elements must be protected. Trade secrets are one way of obtaining such protection, in addition to registered property rights (such as patents, designs and trademarks) and unregistered ones (such as copyrights in our legal system).
- In order to benefit from protection, adequate implementation of the requirements for trade secrets is necessary, as the law once again emphasizes and reinforces.
- The protection of trade secrets takes place on three levels: (1) by appropriate organization, planning and guidelines, (2) by restricting access to secrets, and (3) by appropriate contractual agreements.
- For implementation, an information security system should be set up and usually several contracts have to be adapted, this article also explains details on this.

What is a trade secret?
One of the most prominent trade secrets is The Coca-Cola Company's Coke recipe. The company, which Asa Griggs Candler bought in 1892, continues to keep secret the recipe, which dates back to chemist John Stith Pemberton's work in 1886. The success of the company is therefore still to a significant extent based on this trade secret (the other elements visible to the outside world are the extremely strong brand and consistent quality, regardless of the place of purchase by the customer—Coca Cola Coke is Coca Cola Coke worldwide; "Coke" and "Coca Cola" are registered trademarks of The Coca Cola Company).
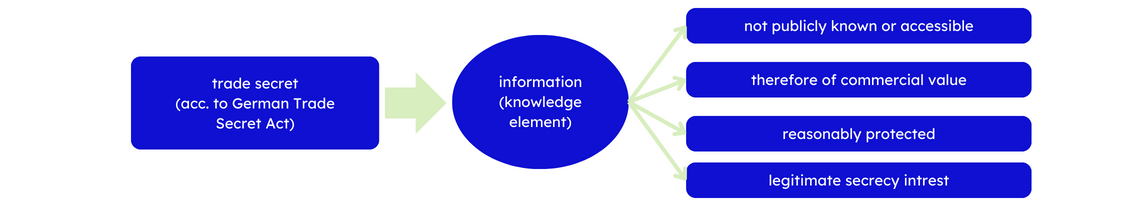
Legally, a trade secret is "information", i.e. an element of knowledge that meets the following criteria (Art. 2 No. 1 Trade Secret Directive (EU) 2016/943):
- It is not generally known or readily accessible;
- it is of commercial value; and
- it is adequately protected (by responsible persons);
- according to German law, the owner additionally needs to have legitimate interest in its secrecy.
It is decisive that the knowledge element is neither generally known nor accessible and is adequately protected. The fact that such an element of knowledge embodies a commercial value is usually induced by the effort the secret's owner makes to protect the secret. In individual cases, this criterion can lead to the exclusion of information that is objectively not valuable and therefore not worthy of protection. Cases in which a legitimate interest in secrecy is lacking may also remain a rare exception (in the legislative process, information on tax evasion models has been mentioned as example). Therefore, it is key for owners of secrets to take suitable and at least substantially effective measures to ensure secrecy.
According to the formal definition in § 2 GeschGehG (German Law on the Protection of Trade Secrets),
A trade secret is a piece of information which
(a) is, neither as a body, nor in the precise configuration and assembly of its components, generally known or readily accessible to persons in the circles normally handling this type of information and therefore is of economic value; and
b) has been subject to reasonable steps under the circumstances, by the person lawfully in control of the information, to keep it secret; and
c) for which there is a justified interest in confidentiality;
Outstanding features of protection of a trade secret
Compared with other legal mechanisms protecting so-called "intellectual property", a trade secret has the following distinctive features:
- Protection automatically applies when new (valuable) knowledge is created and this knowledge is adequately kept secret— no further activities related to the specific knowledge, such as registration or similar, are required.
- Since no further activities are necessary, there are no direct costs to protect it (only general costs for setting up an organisational set-up for information protection, i.e. an information protection management system, apply).
- It is only protected as long as it is not generally known. Accordingly, it loses protection if it is learned by persons without a confidentiality obligation (the limit depends on the individual case).
- Similarly, there is no protection against other persons independently learning the same knowledge.
- It remains protected as long as it is secret and valuable — there is therefore no legal maximum protection period.
- The degree and scope of protection and, in particular, the possibilities of intervention differ more strongly outside Europe, because trade secrets, as trademarks and patents, are not subject to (partial) standardisation by international treaties. Some legal systems potentially even allow industrial espionage to obtain such trade secrets.
Effective protection—how to safeguard your trade secrets
Only knowledge subject to "appropriate security measures" is protected as a secret. These protective measures themselves keep the knowledge secret and thus serve the company's own purposes. Such measures should be systematic, comprehensive and documented to be able to serve as evidence in the event of legal proceedings. To make the procedures comprehensive, an appropriate system for the entire company or at least a business unit should be taken rather than specifically protecting each single piece of information.
Please note: to the current legal situation in the EU generally permits reverse engineering. This is a significant change compared to the previous German legal situation, according to which it was at least unclear whether reverse engineering was permissible in individual cases. Therefore, it is often permissible to analyse a product with regard to its properties to such an extent that, for example, the secrets required for production can be extracted from it. Although not unlimited in effect, this can be addressed by suitable contractual agreements, namely by prohibiting the contracting parties from carrying out precisely such analyses. It is not yet certain to what extent the courts will accept such clauses in the long run; nevertheless, it is worthwhile taking the measure, especially since secrets otherwise remain unprotected and such clauses themselves hardly pose additional risks.

Systematic handling of trade secrets
The protection of trade secrets in the company's own (direct) best interest, as well as for the purpose to achieve legal protection as trade secret, mandates for action. The most important activities are:
- Identify business-critical, non-public knowledge.
- Define the types of knowledge within the company.
- Define the scope of action for the parties involved.
- Implement access restrictions (see following section).
- Establish contractual arrangements (see next but one section).
- First of all, the organisational set-up is important. If it is unknown where the core secrets of your own business lie, they cannot be protected in a meaningful way.
An adequate agreement is helpful to effectively protect trade secrets, regardless of whether it is concluded with employees, with partners in purchasing, sales or in joint development settings. The purpose of a confidentiality agreement is to enable a contractual partner to disclose information without losing the legal protection of the information as trade secret. Within such agreements, the contractual partners also agree on the limits within which the disclosed information may be used. A holder of a secret regularly shares secret information only if it has been clearly agreed with the receiving party what may and may not be done with the secret information.
In cooperations, confidentiality agreements drawn up according to current standards are suitable for this purpose. In addition to other important topics, they now need to regulate the topic of reverse engineering, for example with a clause like this:
Prohibition of reverse engineering
The products provided must not be examined with regard to their chemical, biological, physical and technical properties and structure; in particular, they must not be dismantled or observed, examined and tested beyond the requirements of the application.
Access protection ("technical protection")
The technical implementation of access restrictions is a necessary part of the trade secret protection setup and includes:
- Access regulation
- Authentication and authorization of each user access
- Clear prohibition to gain access to information not necessary for one's own work activities and enforcement of this prohibition; this includes the renunciation of IT accesses shared by several persons (user accounts).
Contractual protection
Adequate protection can only be achieved if all partners and individuals are contractually obliged to secrecy. In particular, the following contracts should be examined to verify whether they contain the appropriate clauses—if they do not, they should be supplemented where possible:
- Employment contracts
- Supplier contracts
- Sales/customer contracts
- Confidentiality agreements, in particular with regard to whether the prohibition of reverse engineering is correctly implemented
- Cooperation agreements, especially in the context of research and development
Are you looking for legal support on an equal footing? Get in touch with us.
Questions and answers
Employees are generally obliged not to harm their employer; this is an implicit ancillary obligation under their employment contract (contractual duty of good faith). However, this duty is blurry and its scope is not well defined. Worse still, not giving instructions misses a clear instruction regarding the desired behaviour. Thus, trade secrets are endangered both practically (lack of instruction) and legally (by uncertainty as to whether a certain action is really prohibited). For this reason, it is important to include appropriate provisions in employment contracts and to include them anew or corrected if necessary.
The law provides for certain acts as generally permitted (in § 3 GeschGehG, German Law on Trade Secret Protection):
own developments,
reverse engineering (under certain conditions, which are, however, quite extensive, see the following question) and
within the framework of employee representation (to exercise information and consultation rights of employees or participation and co-determination rights).
The law also permits certain otherwise prohibited actions (§ 5 GeschGehG) by way of exception in the case of (legally) justified interest:
for the implementation of the expression of opinion and media work (as well as associated freedom of information),
"whistle blowing" (for the detection of illegal activities/grave misconduct for the protection of the public interest) and
in cooperation with employee representatives (to the extent necessary for the legally assigned tasks).
However, everyone intending to rely on such exceptions should exercise caution as they are regularly interpreted narrowly. The above description is aimed at general comprehensibility and not at legal precision—it may therefore deviate from the applicable law in certain subtleties—in case of doubt (at least) read the law, because (only) this is applicable.
In the earlier legal situation in Germany, the dismantling of products for the purpose of extracting trade secrets was largely prohibited and punishable under the Law against Unfair Competition (Gesetz gegen unlauteren Wettbewerb, UWG) (a key decision was the "Stiefeleisenpresse" decision, the name of which already reveals its age). This has changed significantly with the GeschGehG on the basis of the 2016 European Directive on the Protection of Trade Secrets: for the purpose of strengthening competition and for European standardisation's sake, "reverse engineering" has been permitted largely in the Directive, provided that the corresponding product was legally acquired (cf. Art. 3 para. 1 (b) of Directive (EU) 2016/943) and no contractual restriction exists (cf. § 3 para. 1 no. 2 GeschGehG). Thus, in many cases, the existence or absence of contractual usage restrictions will determine whether a product may be reverse engineered.
Not necessarily. It is of course true that a secret becomes less secret the more people know it. For trade secret protection, it is therefore necessary to keep the circles that know any given secret as small as possible. Only those who need to know a secret for their work purposes should know it. At the same time, it can be useful to share secret information with partners if this opens up significant business opportunities. However, the partners must be selected with particular care for this purpose and they must be obliged to treat the trade secrets adequately (in particular not to pass them on to third parties and also to use them only for the contractually intended purpose).
Furthermore, the new law set changed provisions for the (necessary) disclosure of trade secrets in court proceedings. Even in (basically public) trials, the law now enables to avoid disclosure of trade secrets, e.g. because court files are blackened, can be heard in non-public proceedings and court decisions are only published to a very limited extent.
Basically, this does not change any requirements: it doesn't matter where exactly the data is stored or who runs the servers, but how the data is protected. Depending on the setup, the cloud can even offer strong advantages, as the providers usually have significantly better resources in the area of IT security. In addition, a good solution can be to encrypt the data before it is transferred to the cloud and to keep it encrypted throughout the entire processing (as far as the application allows this). In any case, however, it is important to select the providers carefully and to agree suitable contractual arrangements and to avoid unsafe environments, such as storage in IP critical jurisdictions.
Downloads and materials
Please find further information and tools here:
- A simple questionnaire as Excel file or on Google Forms (both currently German only, please contact the author in case of need of an English version) (Please use the Excel version if you do not wish your data to be shared with Google or do not agree with the Google Privacy Policy; in case you use the online form, I will send an evaluation as soon as reasonably possible.) – I further offer an extended Excel tool with concrete recommendations for action as bundled with a fixed price consultation package at a reasonable fixed price.
- Legal text of the Gesetz zum Schutz von Geschäftsgeheimnissen - GeschGehG (German Act on the Protection of Trade Secrets – German language document) and the Directive on the protection of confidential know-how and confidential business information, business secrets, against unlawful acquisition, use and disclosure
Note: The legal protection of trade secrets is only one possible path to protect relevant information and results in their commercial value. In addition, registered intellectual property rights such as trademarks, designs and patents, and unregistered ones such as copyrights and similar rights are relevant. Please to contact us if you wish to know more.
This article does not replace legal advice in individual cases. It presents the situation from a German legal perspective — the situation in other jurisdictions may differ.